This is going to be a short post about how to generate CA certificates and import it to store to be used by popular clients such as: chrome or cURL. I'll try to show all main points to go through. Of course, as always, all will be provided with example to make the life easier.

CA
What is CA (Certificate Authority)? Roughly speaking, this is a special certificate type which are being used to sign a signing requests which finally produces certificates ready to use in i.e. web server.
Get CA - Certificate Authority
The easiest way to get the CA is to download from some secure folder or Vault. This is common way of working in case then you have access to CA which mean you can sign certs by your own.
az keyvault secret show --subscription <SUBSCRIPTION> --vault-name <VAULT> --name <NAME> | jq -r
Unfortunately, in the most cases you are not eligible to have access to CA. Nevertheless, you still can read this post and you will find information for you.
First of all, you have still two options
- Generate Self-signed CA
- Ask Security guys to sign your certificate
All these two cases I'll be explaining in the next paragraphs.
Self-signed CA
Self-sign CA certificate is a common practice in the development environments (not for prod). In this case, you have to start with generating a private key.
openssl genrsa -des3 -out CA.key 2048
One commend to this. During generating the key you can protect it using password. To check if your private key is additionally encrypted you can find that information at the beginning of the content of the file
$ cat CA.key -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: DES-EDE3-CBC,D8B9F8CD5B599AB3 [...]
Once you have private key generated you are ready to generate CA certificate. To do that please run following command
openssl req -new -x509 -nodes -days 1825 -key CA.key -sha256 -out CA.pem
As a result, we have our own CA. It means that from now we can sign another certificate requests. We can produce as many certificates as we need.
Import CA to store
But hold on for a second. Before you move anywhere you have to do one but really important task. You have to add CA certificate to your store which is used be your client like web browser or cURL
Windows
In Windows we have many options
- certutil
This is powerful command line tool with many options. We need to get familiar with only two 🙂
To show the imported already CA please run the following command
> certutil -store Root
To import CA (either DER or PEM format) please run the following command
> certutil -addstore "Root" CA.crt > certutil -addstore "Root" CA.pem
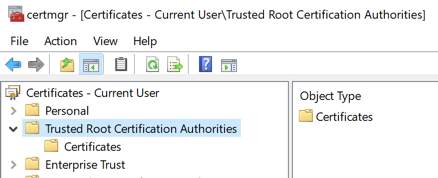
- certmgr
This is GUI tool (I would call it - clickable). You can examine all the trees with the certificates but the most important is Trusted Root Certification Authorities. This is a please where CA should be placed. Before you try to import the cert inside change the format to DER. Below command will do it for you.
openssl x509 -outform der -in CA.pem -out CA.crt
And that CA.crt you can import to Trusted Root Certification Authorities
- PowerShell
Yap, no surprise , in Windows you can perform anything using PowerShell. To list the certs you can use Get-ChildItem Swiss army tool 🙂
Get-ChildItem Cert:\LocalMachine\Root
Import aren't over-complicated (Either DER or PEM format)
Import-Certificate -FilePath CA.crt -CertStoreLocation Cert:\LocalMachine\Root # or Import-Certificate -FilePath CA.pem -CertStoreLocation Cert:\LocalMachine\Root
Linux
In Linux environment (using cURL) you can fetch page over HTTPS with CA by passing it as a argument.
curl --cacert CA.pem https://your.domain
However, this is not an elegant solution. Much better is to add to store. It was the hardest part for me for ages but some day I spotted that post
Copy your certificate in PEM format into
/usr/local/share/ca-certificatesand name it with a.crtfile extension. Then runsudo update-ca-certificates.
And now you can use curl without additional parameter at least for one more page 🙂
Summary
Having CA in the store and page exposed over HTTPS using certificate signed by our CA you have
- secured communication
- no red monit in web browser
- no asking for certs in cURL
